Cyber Security

Security Products & Services:
End point protection
Firewall
Email Security

Cloud native security
MDR Managed Detection & Response
XDR Detection & Response

Compromise Assessment
Penetration Testing
Compliance & Consulting
HOLISTIC APPROACH FOR INCREASED INFORMATION SECURITY

Cybersecurity attacks focus on vulnerabilities of IT systems, internal and external networks, and employees’ level of readiness and awareness to recognise such attacks.
With the increasing complexities of IT systems, digital transformation, and huge demand for accessibility by employees, we take a holistic approach to cybersecurity measures including data, applications, systems, networks, and human factors.
Initially, we conduct a comprehensive investigation and review of all systems with potential vulnerabilities with appropriate counter-measures and assess employee awareness through cybersecurity training and phishing simulation.
All IT systems externally accessible are tested for any vulnerabilities, including internal networks and their connections, should an attacker gain access to internal IT systems and provide measures for both, stopping such attacks and preventing them from spreading across internal networks.
Subsequent steps create an optimal basis for securing the entire IT landscape. In addition, further measures can be defined and implemented on a risk-based basis.

1. The human factor
Phishing Simulation
- Evaluation of your employees’ roaction to different scenarios
- Human risk factor becomes measurable. Awareness Training
2. External Perimeter
Vulnerability Assessment & Penetration Testing
- Roview of all IT systems accessible externally (from the Internet)
- Overview of risks and vulnerabilities of externality systems
3. Internal IT Systems
Vulnerability Assessment
& Penetration Testing
- Comprehensive review of IT systems and applications
- Demonstration of vulnerabilities & configuration deficiencies in IT systems and applications
4. Advanced Measures
Implementation of Measures IT security Assesments
- Customized support based on
assessment results.
HUMAN KPI – MAKE SECURITY AWARENESS MEASURABLE
PHISHING SIMULATION
Technological safeguards alone are not enough to protect your business from cybersecurity attacks. Nowadays, humans are increasingly being targeted by attackers. One of the most common attacks is aimed at deceiving employees into obtaining confidential information. Such phishing attacks are becoming increasingly sophisticated.
We offer you the opportunity to carry out tailor-made phishing campaigns to evaluate the reaction of your employees to different attack scenarios. Through continuous training and awareness-raising measures, your company achieves a significantly higher level of information security.
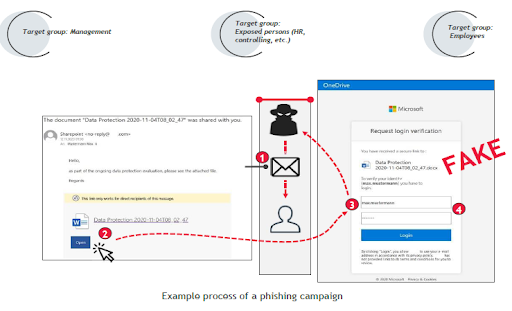
DANGERS OF PHISHING ATTACKS
Phishing attacks are a serious threat to your entire business. Fraudsters are often very targeted. It is therefore often difficult for employees to distinguish legitimate emails from phishing emails. Successful phishing attacks usually result in the execution of ransomware and significant damage to the company!
TARGET GROUPS
Depending on the type of phishing emails, the target groups also differ. It therefore makes sense to develop different scenarios for individual target groups to gain as realistic an impression as possible with regard to the awareness of your employees.
AWARENESS TRAINING
INFORMATION SECURITY STARTS WITH THE HUMAN FACTOR
For years, the lack of sensitivity of IT users about information security has been complained about. A technically secure IT infrastructure is not enough to ensure the security of your company.
Therefore, support your employees in dealing with possible attacks with know-how and thus ensure that they are detected and fended off. With the help of our security awareness training, your employees learn how to identify potential dangers and avoid risky behaviour in everyday work. In this way, they prevent, among other things, financial damage, reputational losses, and possible legal consequences due to the GDPR.
MODULAR DESIGN
The interests and problems of a company are usually of different nature. Therefore, in addition to comprehensive basic training, we also offer independent, in-depth modules so that you benefit from the greatest possible added value. We take over the creation of the Course content as well as the design of the Training and coordination according to you our customers’ requirements.
WHY POINTEC?
- Years of expertise: Our security awareness Coaches have years of expirience in conducting IT security training. They Impart profound Technical knowledge and provide a wide range of information about the latest threats.
- Practical relevance: Your employees are involved in the training in the best possible way in face-to-fae training in order to acheive the greatest possible learning success trough learning-by-doing and to better understand complex relationships.
- Live hacking demonstration: To help your Employees better understand possible attacs, we provide live information on ho to deal with criminal attacs.
VULNERABILITY ASSESSMENT & PENETRATION TEST
ATTACKS START WITH INTELLIGENCE GATHERING
Attackers scout systems and first look for easy-to-exploit vulnerabilities – so-called low-hanging fruits. A vulnerability scan identifies and classifies such vulnerabilities in your IT systems, which checks the effectiveness of existing countermeasures and allows you to react to new vulnerabilities.
A penetration test also focuses on the detailed manual inspection of individual systems. For example, serious security gaps in access controls of web applications can be uncovered. This enables you to identify possible attack vectors and secure your system or application in the best possible way.
VULNERABILITY ASSESSMENT
Vulnerability assessments provide an overview of possible vulnerabilities in IT systems. With the help of (partially) automated scans, as many potential vulnerabilities as possible are uncovered.
Vulnerability assessments can be carried out for IT systems and services accessible from the Internet as well as for your internal networks. In order to identify many attack vectors, we examine a large number of systems. In this way, as many low-hanging fruits as possible are shown within your IT systems and services. All identified IT systems and their weak points as well as the necessary measures to remedy them are shown in a report for you.
PENETRATION TEST
As part of a penetration test, we carry out a comprehensive examination of your IT systems or applications (e.g. webshop, customer portal) including corresponding application logic.
It traces the path that a potential attacker would take in order to detect any remaining weaknesses in your IT systems and networks. Identified vulnerabilities are deliberately combined or exploited, e.g. to obtain higher user rights or confidential information.
Our task is to check your IT systems and application design with regard to possible attack scenarios and to document findings in a detailed report for you.
REMOTE ACCESS
The corona pandemic has accelerated and driven companies’ digitization projects. Ways to access resources outside the company’s own network were set up within a few days. However, remote access in particular carries a very high risk for companies.
For example, we check whether access has been secured in the best possible way and whether access to company secrets is correctly restricted.
WEB APPLICATIONS
Thorough manual review of individual web applications or APIs. The aim is to identify security-relevant configuration errors and vulnerabilities in the program logic, or the software used, with the help of which damage could be caused.
INTERNAL NETWORKS
From zero to hero. We simulate an attacker who already has access to the internal network and try to gain the highest possible privileges. Ideally (for us) the penetration test ends with domain admin permissions.
